Routing Internet traffic through a site-to-site OpenVPN-connection in PfSense software version 2.1¶
This article shows how to create a site-to-site connection using OpenVPN and how to route the Internet connection of site A through site B using pfSense® software.
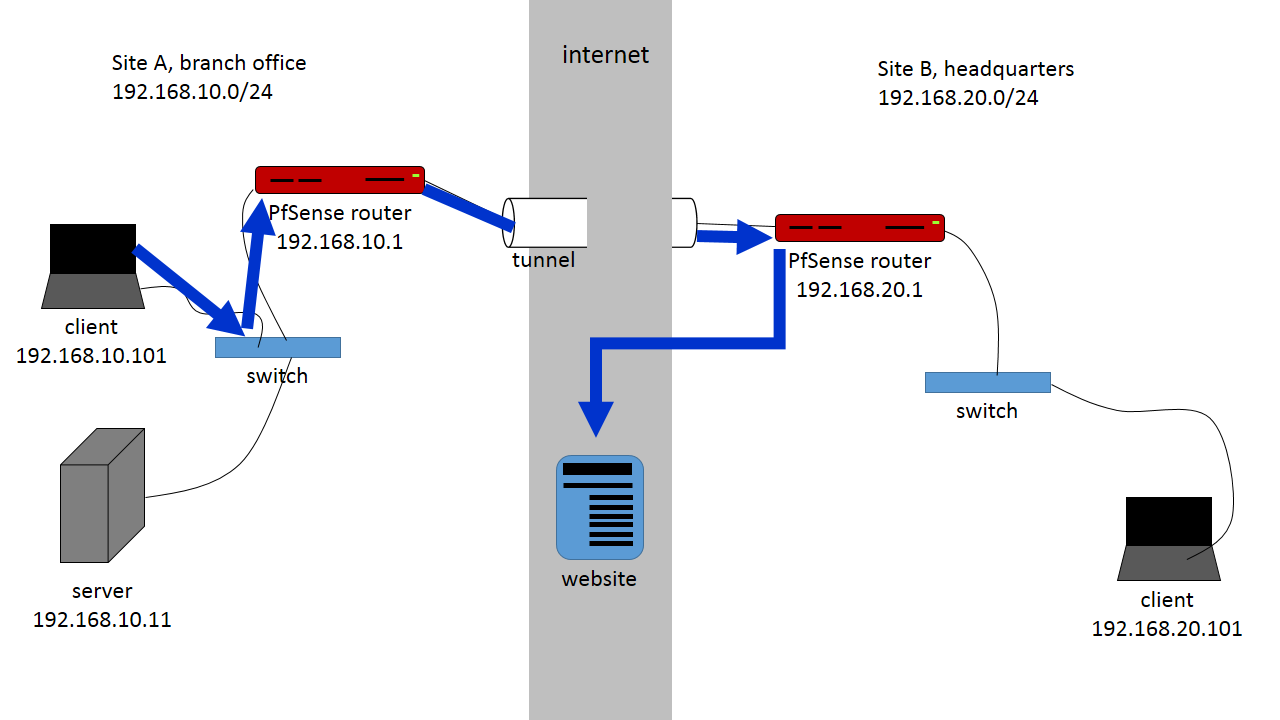
This is effectively the same as using an IPsec site-to-site connection except that we’ll be using OpenVPN instead of IPsec. Using OpenVPN as the ‘back-end’ means we need to set up one side as a server and the other as the client. It doesn’t matter which one is which but if more than two sites are connected in a star topology it seems natural to use the center of the star as the server. The server also needs to have a dedicated port mapped to it if it’s behind another router, or is must reside in its DMZ.
For the purpose of this article:
Site A is a branch office, LAN subnet 192.168.10.0/24
Site B is the main office through which all Internet traffic is routed, 192.168.20.0/24
Set up OpenVPN at Site B¶
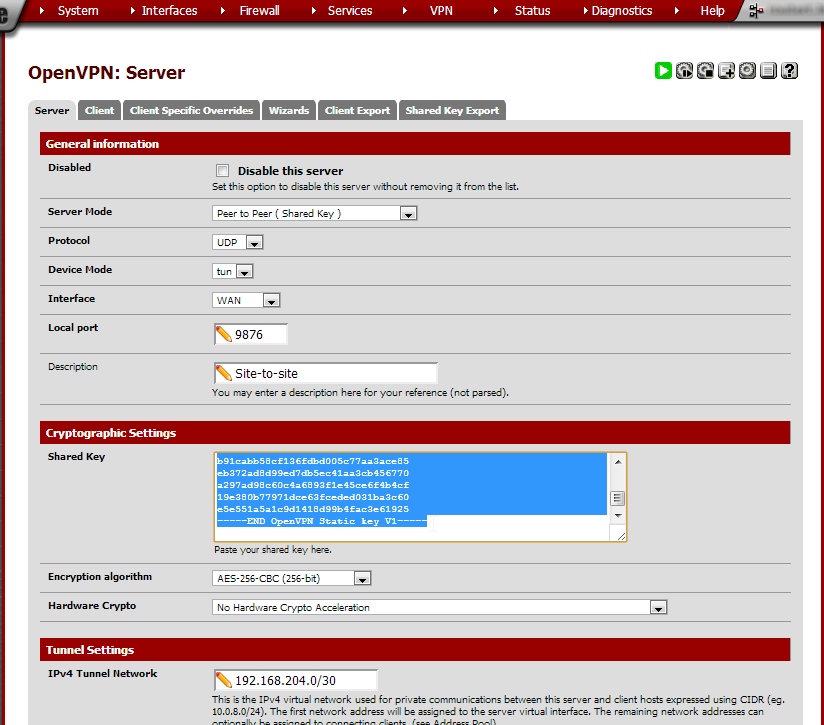
From the VPN menu choose OpenVPN. On the page under the Server tab, click the + button to create a new OpenVPN server.
Enter these values:
Server Mode |
Peer to Peer (Shared Key) |
|
Protocol |
UDP |
|
Device Mode |
tun |
|
Interface |
WAN |
|
Local port |
9876 |
1194 is the default OpenVPN port. It doesn’t hurt to change it to another number to add some security through obscurity. Any unused port number may be used but we’ll stick to 9876 in this article. |
Description |
Site-to-site |
|
Shared Key |
Checked |
|
Encryption algorithm |
AES-256-CBC (256-bit) |
|
Hardware Crypto |
No Hardware Crypto Acceleration unless it is needed for this hardware. |
If in doubt, select ‘No Hardware Crypto Acceleration’. |
IPv4 Tunnel Network |
192.168.204.0/30 |
Choose a subnet that’s not in use in any of the current LANs. This will be used internally by OpenVPN. We’re using 192.168.204.0/30 here but any private range will do. The /30 mask is because OpenVPN will only use one IP address per site. We’re connecting two sites so two addresses will suffice. /24 will work but is overkill. |
IPv6 Tunnel Network |
leave empty |
|
IPv4 Local Network/s |
192.168.20.0/24 |
Site B’s subnet |
IPv6 Local Network/s |
leave empty |
|
IPv4 Remote Network/s |
192.168.10.0 |
Site A’s subnet |
IPv6 Remote Network/s |
leave empty |
|
Concurrent connections |
leave empty |
|
Compression |
Check if the bulk of the data transferred will be uncompressed data, like Office documents. Leave unchecked if the bulk is already compressed, like divx films. Routers on faster hardware can compress faster. |
|
Type-of-Service |
unchecked |
|
Duplicate Connections |
unchecked |
|
Advanced |
leave empty |
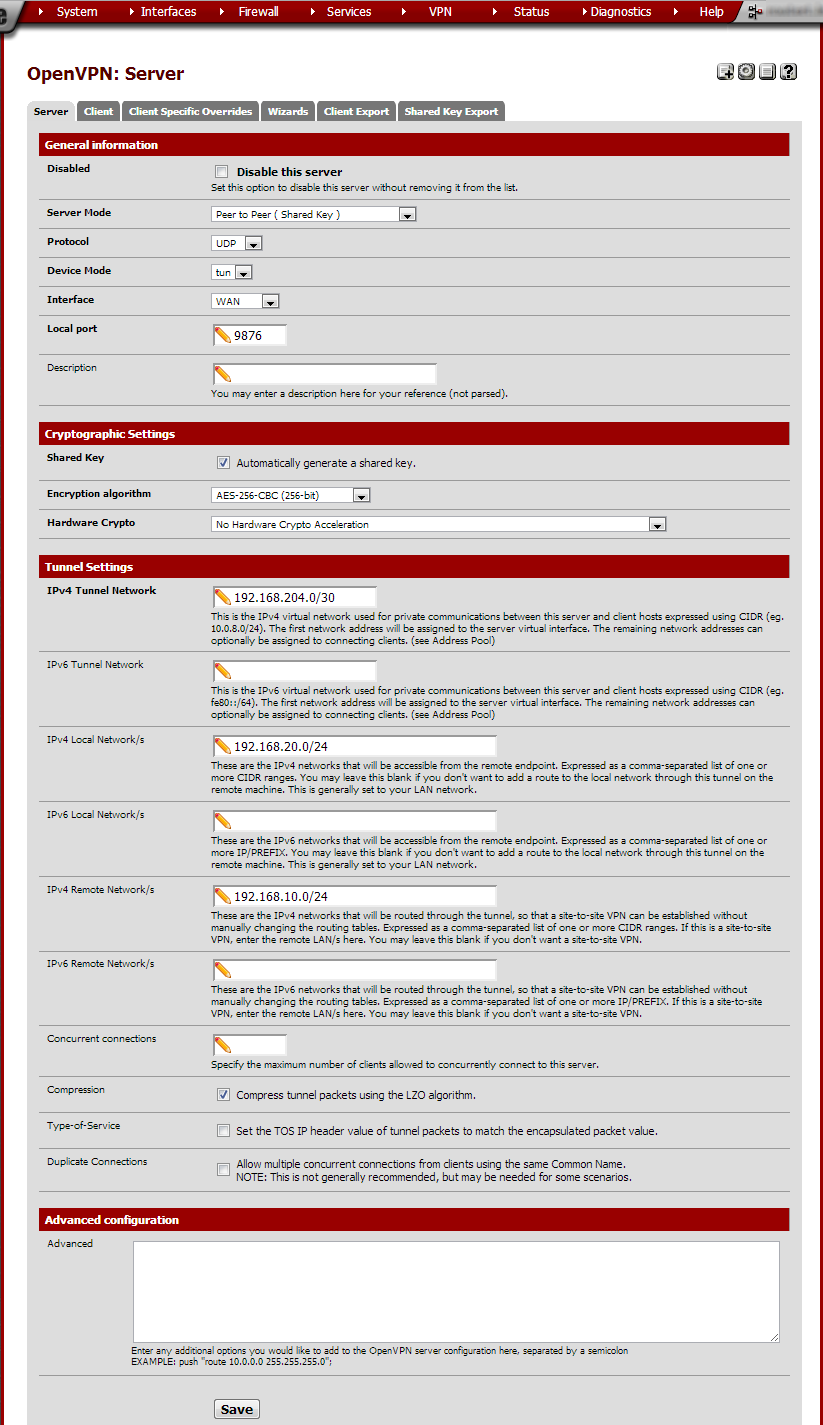
Click Save.
Note that our Site-to-site OpenVPN server is now shown in the Server overview. Click the edit button to the right of the server.
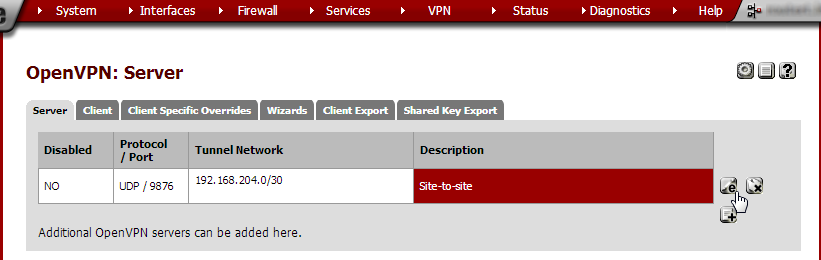
Note that in the Cryptographic Settings section, a Shared Key is now shown. Copy all text in the Shared Key text field, including the first lines beginning with # and the last line ending in —–.
Configure firewall rules at Site B¶
From the Firewall menu, choose Rules. Open the WAN tab, unless using a different interface for the VPN connection. Click on the + button to add a new rule.
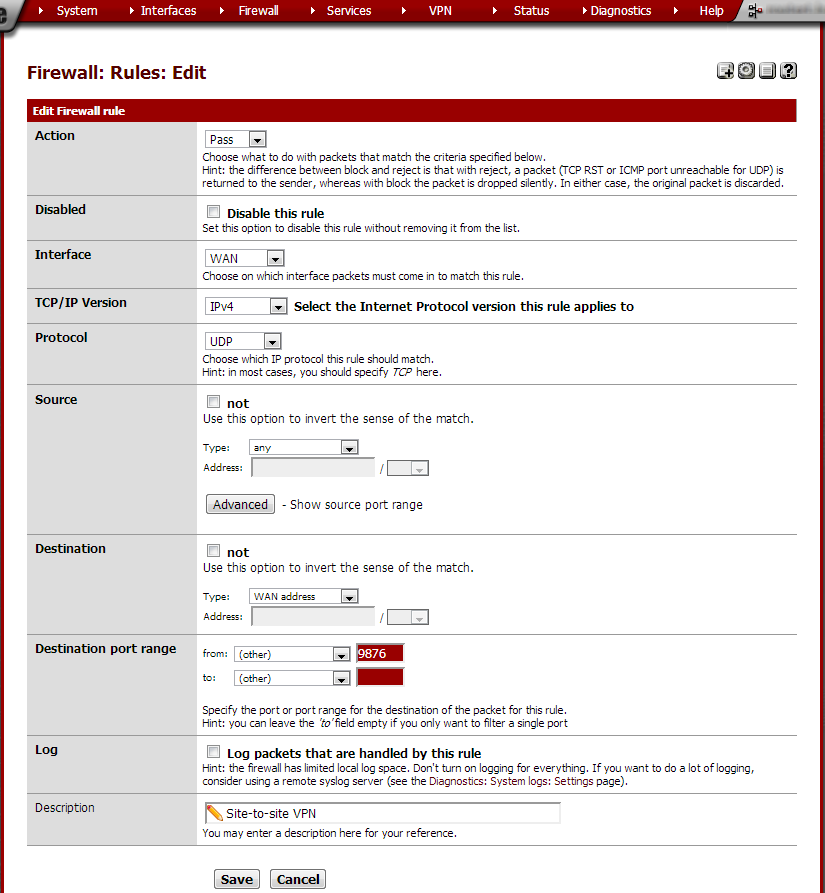
Enter these values:
Action |
Pass |
Disabled |
not checked |
Interface |
WAN |
TCP/IP Version |
IPv4 |
Protocol |
UDP |
Source |
any |
Destination |
Type: WAN address |
Destination port range |
from: (other) 9876 to: (other) |
Log |
not checked |
Description |
Site-to-site VPN |
Click Save and on the next page click Apply changes.
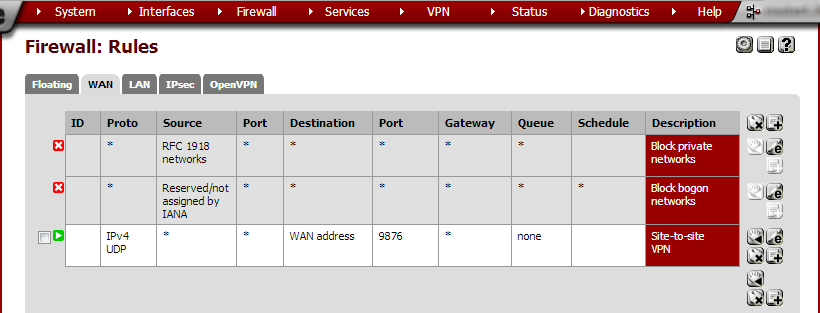
Click on the OpenVPN tab. We’ll now add a rule to allow traffic through the OpenVPN connection. Click on the + button add a rule.
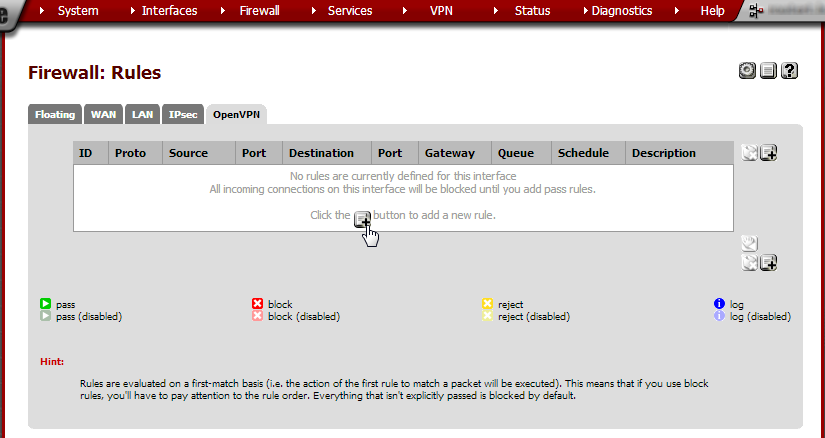
Enter these values:
Action |
Pass |
|
Disabled |
not checked |
|
Interface |
OpenVPN |
|
TCP/IP Version |
IPv4 |
|
Protocol |
any |
|
Source |
any |
|
Destination |
any |
|
Log |
not checked |
|
Description |
Allow everything through OpenVPN |
Click Save and on the next page Apply Changes.
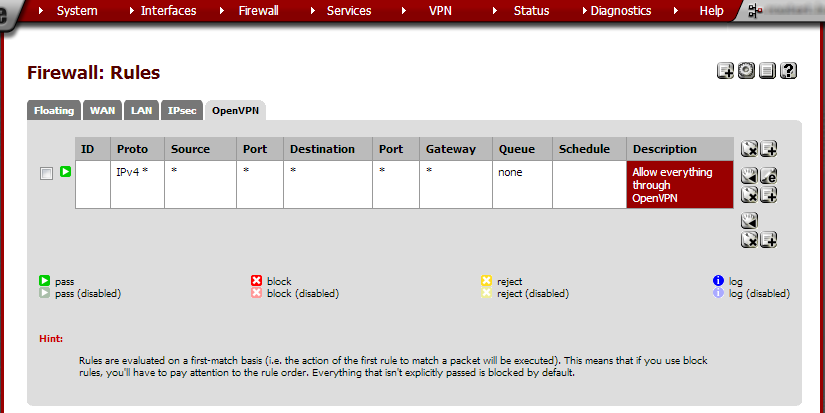
Set up outbound NAT at Site B¶
From the Firewall menu, choose NAT and click on the Outbound tab. Select Manual Outbound NAT rule generation (AON – Advanced Outbound NAT) and click Save. On the next page, click Apply Changes.
A couple of rules are generated automatically but we need to add a NAT entry for Site A’s subnet. Click on the + button.
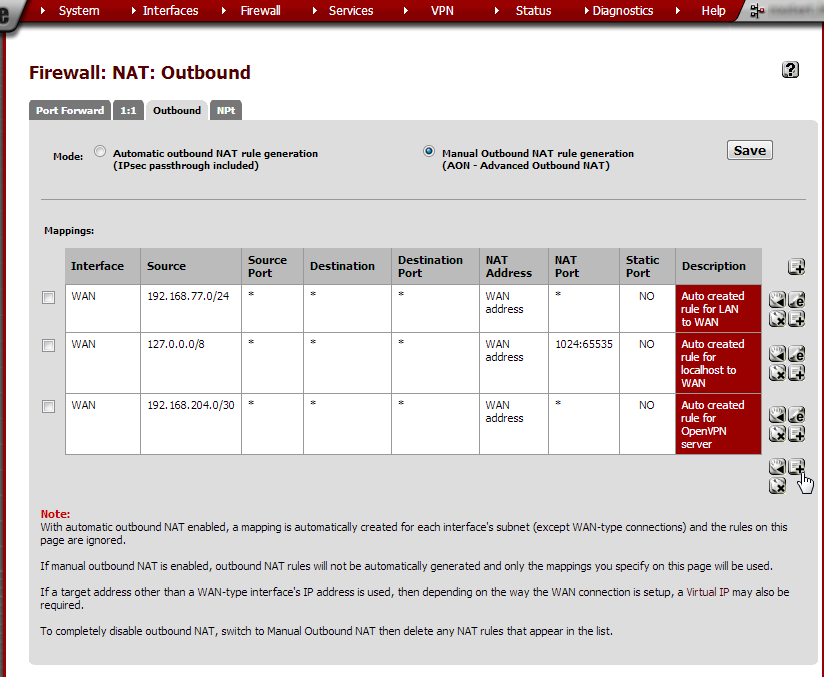
Enter these values:
Do not NAT |
not checked |
|
Interface |
WAN |
Unless using a different interface for the VPN |
Protocol |
any |
|
Source |
Type: Network Address: 192.168.10.0/24 Source port: leave empty |
Site A’s subnet |
Destination |
Type: any Destination port: leave empty |
|
Translation |
Address: Interface address Port: leave empty Static port: not checked |
|
No XMLRPC Sync |
Leave unchecked |
|
Description |
Site A |
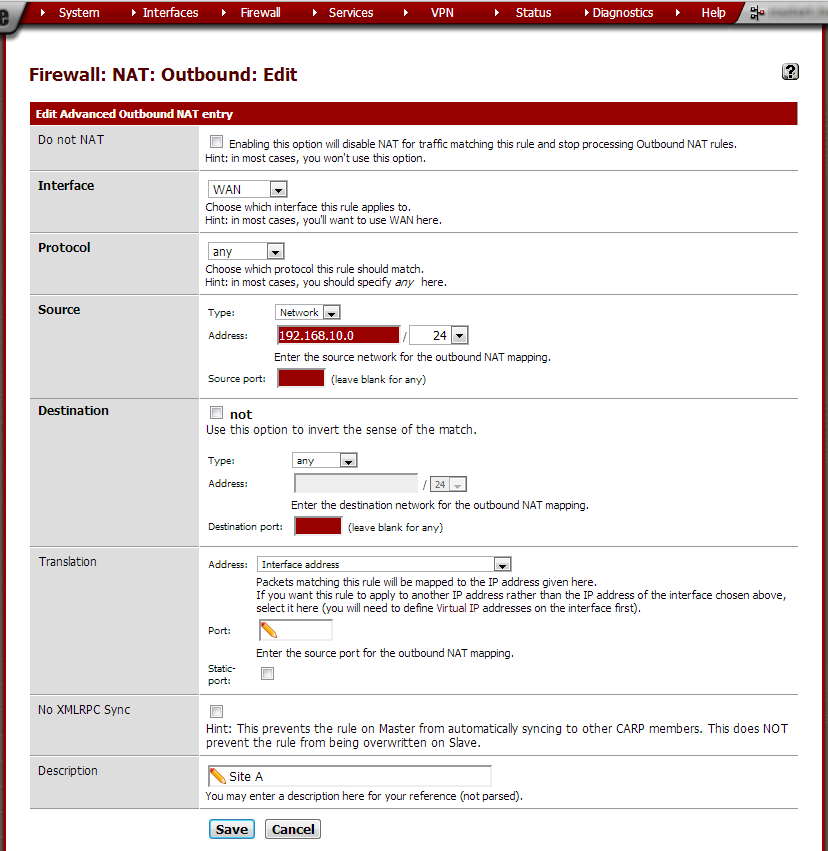
Click Save and on the next page click Apply Changes.
Set up the client at site A¶
From the VPN menu choose OpenVPN and go to the Client tab. Click the + button to configure a client.
Enter these values:
Disabled |
not checked |
|
Server Mode |
Peer to Peer (Shared Key) |
|
Protocol |
UDP |
same as Site B |
Device mode |
tun |
|
Interface |
WAN |
|
Local port |
leave empty |
|
Server host or address |
Site B’s public IP address or FQDN |
|
Server port |
9876 |
the port Site B is running the OpenVPN server on |
Proxy host or address |
leave empty if not using a proxy |
|
Proxy port |
leave empty if not using a proxy |
|
Proxy authentication extra options |
leave empty if not using a proxy |
|
Server host name resolution |
check if Site B sometimes has connectivity problems |
|
Shared Key |
do not check ‘Automatically generate a shared key’ but paste the Shared Key from site B |
|
Encryption algorithm |
AES-256-CBC (256-bit) |
same as Site B |
Hardware Crypto |
Choose ‘No Hardware Crypto Acceleration’ unless the hardware has an accelerator |
|
IPv4 Tunnel Network |
192.168.204.0/30 |
same as Site B |
IPv6 Tunnel Network |
leave empty |
|
IPv4 Remote Network/s |
192.168.20.0/24 |
site A’s subnet |
IPv6 Remote Network/s |
leave empty |
|
Limit outgoing bandwidth |
leave empty unless required |
|
Compression |
same as Site B |
|
Type-of-Service |
not checked |
|
Advanced |
redirect-gateway def1; |
This makes all traffic, including Internet traffic, go through the tunnel. |
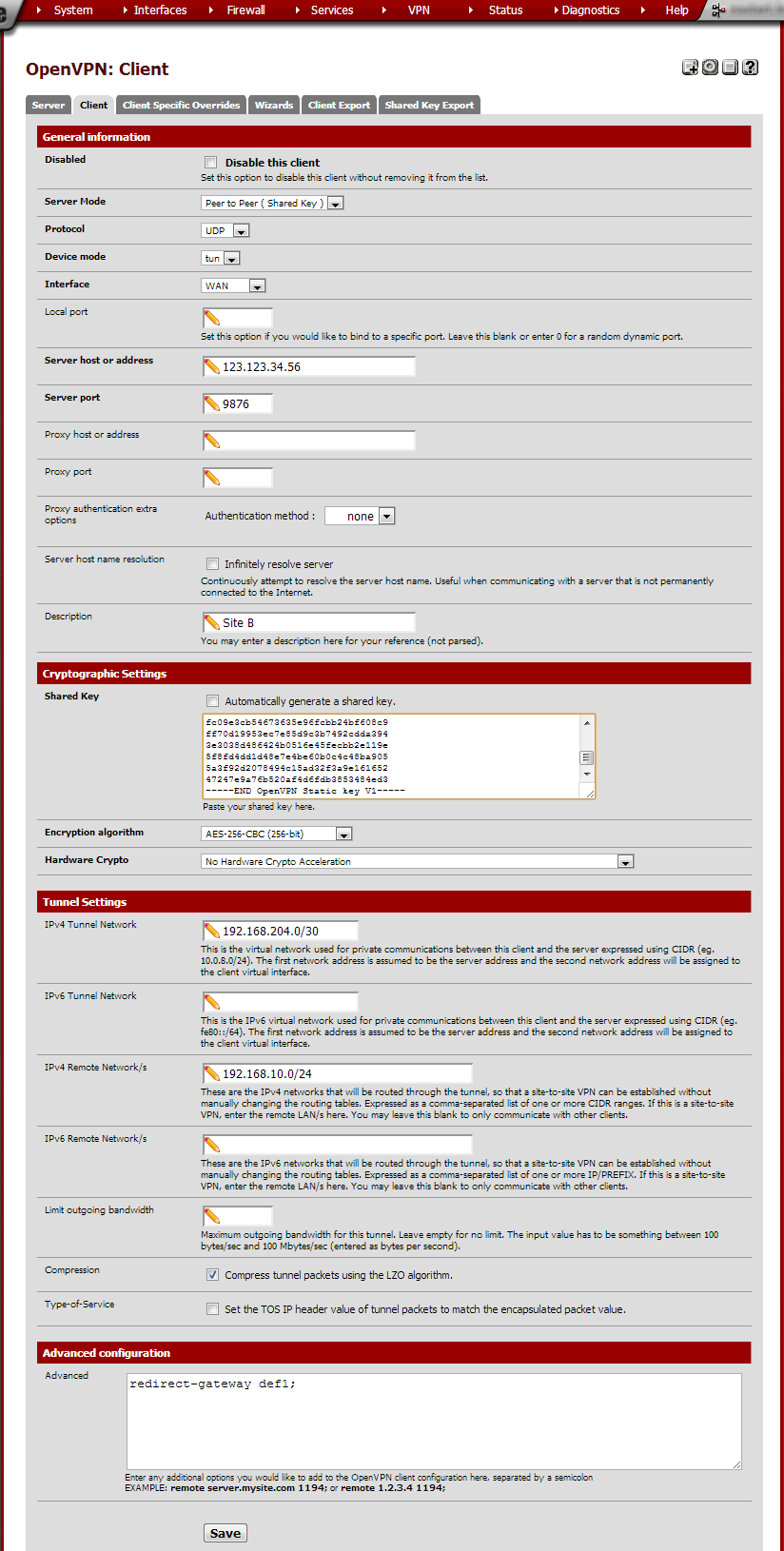
Click Save.
The tunnel should now work and internet traffic should be routed from Site A through the tunnel out site B.
By Vorkbaard, 2013-07-29 - gmail{a}vorkbaard[.]nl